
Discover ways to construct a easy, dependable fame stack so you may spot points early, doc what occurred, and reply quick with out chaos.
Repute used to imply PR, opinions, and the occasional disaster assertion. In 2026, additionally it is your search outcomes, screenshots on social, AI summaries, worker chatter, and affiliate content material you didn’t approve.
The onerous half is just not “having instruments.” It’s having the proper instruments related to a workflow your group will really use when one thing breaks on a Saturday.
This information walks by means of a sensible fame tech stack: monitoring, archiving, alerting, and response workflows that scale back surprises and preserve your model resilient.
What’s a fame tech stack?
A fame tech stack is the set of instruments and processes you employ to:
- Detect new mentions and dangers early
- Protect proof (what was mentioned, when, and the place)
- Route points to the proper proprietor rapidly
- Monitor selections, actions, and outcomes over time
Consider it like safety monitoring, however for belief. You aren’t solely looking ahead to “dangerous press.” You’re looking ahead to something that might change how prospects, companions, or staff understand your model.
Core parts normally embody:
- Monitoring and listening
- Evaluate monitoring
- Change detection (when a web page updates)
- Archiving and proof seize
- Alerts and escalation
- A response workflow and ticketing system
- Reporting and post-incident studying
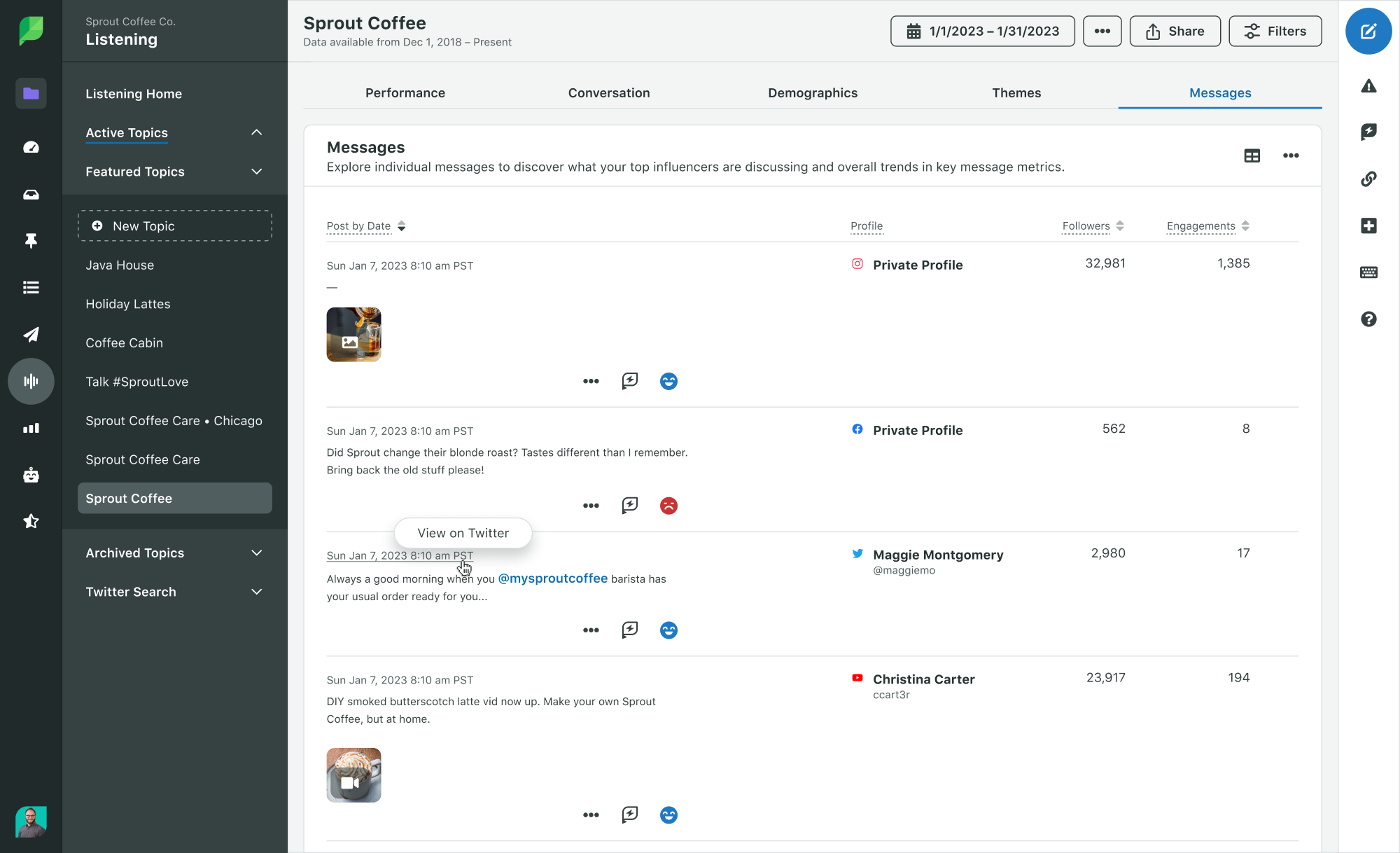
What ought to your stack do each week?
stack runs quietly within the background, then will get loud solely when it ought to.
Right here is the baseline conduct you need:
- It catches new mentions inside hours, not weeks
- It reveals you patterns (one-off criticism vs a spike)
- It saves proof routinely (screenshots, URLs, timestamps)
- It assigns an proprietor and a subsequent step
- It creates a file you may reference later
In case your group nonetheless depends on “somebody noticed it on X,” you shouldn’t have a stack. You may have luck.

The 4 layers of a contemporary fame stack
Monitoring and listening
This layer solutions: “What’s being mentioned, and the place is it spreading?”
Use a mixture of sources as a result of no single instrument sees every part.
Search monitoring: Monitor branded queries, product names, govt names, and customary misspellings. Embrace “rip-off,” “lawsuit,” “refund,” “overview,” and your high opponents in watchlists.
Information and media monitoring: Catch protection, syndicated reposts, and native press pickups.
Social listening: Watch TikTok, Reddit, X, Instagram, LinkedIn, and area of interest boards related to your business.
Neighborhood alerts: Monitor Discords, Fb teams, Substack feedback, and creator communities in the event that they affect your patrons.
Tip: Construct three watchlists: “Model,” “Executives,” and “Danger key phrases.” Hold them brief sufficient that somebody can overview them in 10 minutes.
Archiving and proof seize
This layer solutions: “Can we show what occurred if the content material modifications or disappears?”
You need proof for inner decision-making and for conversations with platforms, publishers, companions, or authorized counsel.
- Screenshots with timestamps: Seize the seen content material and the URL.
- Web page archiving: Save HTML or PDF copies, not simply pictures.
- Change historical past: Monitor when a web page updates, particularly for FAQs, coverage pages, and articles that quietly edit particulars.
- Asset library: Retailer brand-approved statements, FAQs, and escalation templates so you don’t write from scratch beneath strain.
Did You Know? Many high-impact incidents begin as small edits: a headline replace, a brand new remark thread, or a repost that outranks the unique. In case you solely save one screenshot, you typically miss the “earlier than” model that issues most.
Alerts and escalation
This layer solutions: “Who must know, and how briskly?”
Alerts needs to be tied to severity. In any other case, folks mute them.
- Low severity: Every day digest to comms or advertising.
- Medium severity: Rapid Slack or Groups alert to a triage channel.
- Excessive severity: Pager-style escalation (textual content/telephone) to an on-call proprietor.
What triggers an escalation?
- Sudden spike in branded search curiosity
- A high-follower creator mentions your model negatively
- A regulator, journalist, or investor posts about you
- A overview bombing sample
- A unfavorable article begins rating in your model identify
- Buyer assist sees repeated complaints about the identical difficulty
Key Takeaway: Your alerts ought to path to an proprietor, not a bunch. Teams create silence as a result of everybody assumes another person will deal with it.
Response workflow and reporting
This layer solutions: “What are we doing about it, and did it work?”
A dependable workflow consists of:
- A triage consumption kind (what occurred, hyperlink, influence, screenshots)
- A severity rubric (Degree 1 to Degree 4)
- Clear house owners by class (opinions, press, authorized, HR, product)
- A ticketing system (so actions don’t stay solely in chat)
- Submit-incident overview (what we realized, what to alter)
Your reporting ought to present traits, not vainness metrics. Monitor:
- Time to detect
- Time to first response
- Time to decision
- Repeat difficulty classes
- High sources of threat (platforms, companions, areas)
- Search visibility shifts for branded queries
A sensible stack blueprint (easy, then scalable)
You may construct a powerful stack with out shopping for an enterprise suite on day one.
Starter stack (lean groups)
- Monitoring: Google Alerts plus one devoted point out instrument (model + execs)
- Critiques: Google Enterprise Profile notifications plus a overview inbox instrument if in case you have a number of areas
- Archiving: A shared proof folder construction plus a web page seize instrument
- Workflow: A single Slack channel for triage plus a light-weight ticket board (Trello, Asana, or Jira)
- Reporting: Month-to-month snapshot in a doc or dashboard
Progress stack (multi-location or excessive visibility)
- Monitoring: Broader protection throughout information, social, and boards
- Critiques: Centralized overview administration with tagging and routing
- Archiving: Automated seize and alter detection for key URLs
- Alerts: Severity-based guidelines with on-call escalation
- Workflow: Customary playbooks by incident sort plus an incident log
- Reporting: Dashboard that ties points to enterprise influence (leads, churn, conversion)
Enterprise stack (regulated, international, or frequent incidents)
- Monitoring: Full media intelligence plus international language protection
- Critiques: SLA-driven routing and role-based permissions
- Archiving: Compliant retention insurance policies and immutable storage
- Alerts: Built-in SOC-style escalation
- Workflow: Cross-functional incident response with authorized overview gates
- Reporting: Government reporting and board-ready threat summaries
The place removing and suppression match within the tech stack
Not each drawback will be “responded” away. Typically the aim is to cut back visibility of dangerous content material, appropriate misinformation, or request removing when content material violates platform guidelines or the legislation.
Your stack ought to enable you determine which path is life like:
- Reply: When it’s a service difficulty, misunderstanding, or remoted criticism
- Right: When one thing is outdated or factually unsuitable and will be up to date on the supply
- Take away: When content material violates guidelines, privateness requirements, or authorized necessities
- Suppress: When removing is just not attainable, however you may outrank it with stronger belongings
If you’d like a plain-language place to begin for content material removing choices, go to Erase’s web site.
How a lot does a fame tech stack price?
Prices fluctuate broadly, principally primarily based on protection and complexity.
Frequent pricing drivers:
- Variety of key phrases and model entities you monitor
- Languages and nations lined
- Social platforms included (some require premium entry)
- Quantity of mentions and retention size
- Variety of areas (for opinions)
- Automation and integrations (Slack, Groups, CRM, ticketing)
Typical ranges (broad and non-binding):
- Starter instruments: low month-to-month spend, however greater guide effort
- Progress instruments: reasonable month-to-month spend, robust time financial savings
- Enterprise suites: greater spend, deeper protection and governance
Tip: Ask distributors what they don’t cowl. Many instruments look “full” in a demo, then miss the precise sources the place your patrons really speak.

How to decide on the proper instruments for your online business
- Outline your threat floor: Checklist the place reputational threat reveals up for you: native opinions, business boards, app shops, information, worker platforms, accomplice channels, or govt visibility. A B2B SaaS model and a multi-location clinic want completely different protection.
- Choose your “single pane” for triage: Determine the place points ought to land first. For many groups, that could be a Slack triage channel plus a ticket board. Your monitoring instruments ought to push into that system cleanly.
- Determine what should be automated: Automate the components that break throughout busy weeks: proof seize, routing, and reminders. Hold judgment calls human.
- Construct playbooks earlier than you want them: Create brief playbooks in your high incident varieties:
- Evaluate spike
- Damaging article begins rating
- Creator criticism
- Knowledge leak rumor
- Worker allegation
- Product security criticism
Every playbook ought to embody: proprietor, first response, info to assemble, approval steps, and “don’t do” steering.
Take a look at the stack with a drill: Run a 30-minute tabletop train. Instance: “A Reddit thread accusing us of X is trending and a neighborhood reporter is asking for remark.” In case your group can’t discover hyperlinks, seize proof, assign house owners, and draft a response rapidly, repair the workflow before you purchase extra instruments.
The best way to discover a reliable setup (and keep away from widespread traps)
Purple flags that normally trigger wasted spend and missed points:
- All alerts, no triage: The instrument floods inboxes however doesn’t assist route or prioritize.
- No proof seize: You may see a point out, however you can’t protect it reliably.
- Reporting with out motion: Dashboards look good, however no one owns outcomes.
- One instrument promise: Any vendor claiming they “cowl every part” is overselling.
- No integration story: If it can’t connect with your workflow, it is not going to get used.
Inexperienced flags to search for:
- Clear protection map (what sources are included and excluded)
- Simple exports and proof seize
- Position-based workflows (particularly for authorized and HR touchpoints)
- Easy guidelines for routing and escalation
- Sturdy assist and documented onboarding
Repute tech stack FAQs
How briskly ought to we detect a fame difficulty?
For top-visibility manufacturers, hours is the aim. For smaller manufacturers, a each day overview cadence will be sufficient, so long as alerts exist for spikes and high-severity key phrases.
Do we want social listening if we aren’t energetic on social?
Typically sure. Individuals discuss manufacturers the place manufacturers should not current. In case your prospects use Reddit, TikTok, or creator communities to make shopping for selections, listening issues even when posting doesn’t.
What’s the largest mistake groups make with fame instruments?
Alert overload. If every part is pressing, nothing is. Begin with a small set of high-signal alerts, then develop as soon as your workflow is secure.
Ought to fame sit with advertising, comms, or buyer assist?
It needs to be shared, however owned. Many groups place triage with comms or advertising, then route points to assist, authorized, HR, or product primarily based on class. What issues is a transparent proprietor and a transparent escalation path.
Can instruments forestall a disaster?
Instruments don’t forestall crises by themselves. They scale back detection time, protect proof, and make response extra coordinated. That’s typically the distinction between a small difficulty and a multi-week drawback.
Conclusion
A fame tech stack is just not about shopping for the largest platform. It’s about constructing a system that spots threat early, captures proof, routes points to an proprietor, and creates constant responses.
Begin easy: monitoring, proof seize, and a triage workflow. Then scale into automation and deeper protection as your visibility grows.
If you wish to make your model extra resilient in 2026, the most effective subsequent step is to audit what you may have at present, run a brief drill, and repair the gaps that present up beneath strain.
For extra on the most recent in life-style, tradition and journey reads, click on right here.









